Latest Cybersecurity News
Jane Moya • October 31, 2024
Yorb is aware of a multi-stage phishing campaign currently impacting New Zealand organisations.
Compromised email accounts are being used by attackers to send phishing emails. This makes it look like it originates from trusted or known contacts. These phishing emails are being sent via Microsoft sharing invitations. The attacker gains access to a compromised email account, uploads a malicious file to their Microsoft OneDrive/SharePoint, and shares this out to the all the compromised accounts contacts.
What to look for:
- This email is from a known contact or vendor you may deal with every now and again
- The email contains a legitimate
OneDrive share, which leads to a fake document. See below example
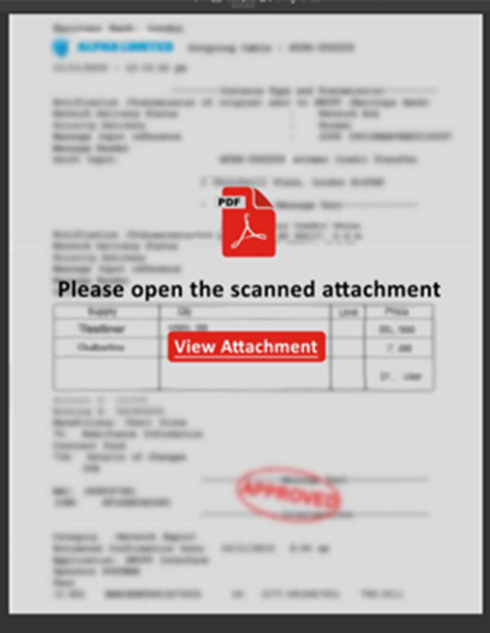
- When you try to open the document, you are redirected to a fake
Microsoft Sign-in page. It may look exactly right but check the URL at the top to make sure it is a Microsoft page. The below are two Microsoft Sign-in pages, can you
spot the fake?
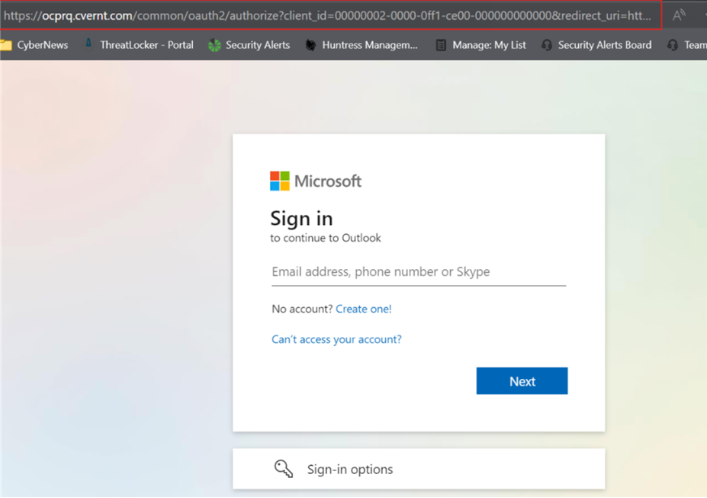
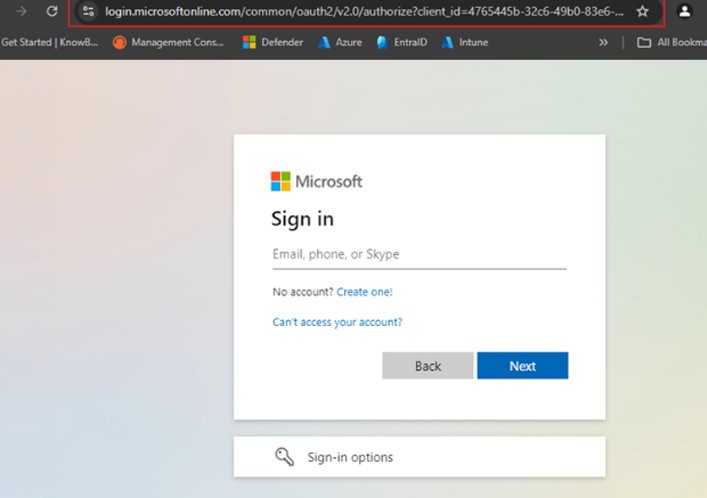
These fake log-in pages are used by attackers to steal your email address and password. It is all happening in real time, so when you enter them in to the fake page, the attacker is entering them into the real Microsoft login page. If you have MFA setup, you will get a prompt, and they will steal this code, or provide you with a number to enter into the Authenticator app thus letting them have access to your email account, and all the company data that you have access to.
The risk of compromise is very serious and can open your organisation up to all sorts of cyber crime. For example, Data Breach, Data exfiltration, Malware, Ransomware, further phishing attacks, Business Account Compromise, Money loss, only to name a few.
Please be vigilant of any sharing links received, especially from external email addresses. If you are not expecting something from the sender, check with them via a different channel. Call them on a phone number from their website, or a cell phone number you might have, or another contact from their company. If you reply to the email, its more than likely the attacker will be the one replying to you.
Remember, phishing attacks come in all shapes and sizes, this is only one type of phishing email that is on the rise now. Use your email awareness skills to check every email, be on the lookout for things that do not seem quite right.
Ask yourself:
- Am I expecting this email from this person?
- Should I verify this email via another contact method?
- Should I be the one to receive this sort of request?
- Why is this request urgent, and the person requesting is saying they cannot be reached?
- This is not normally how we do things, why is this request different?
- If I hover over the link, does it have the link to the site the email says it should?
- Should I check with colleagues, or a third party before continuing here?
- Is this a real email address, and in your Email Directory/Address Book?
Stay Vigilant, Stay Safe!
The Yorb Security Team
Recent Posts




